Dark Helmet: So the combination is one, two, three, four, five. That’s the stupidest combination I’ve ever heard in my life! That’s the kinda thing an idiot would have on his luggage!
[President Skroob walks in.]
Skroob: What’s the combination?
Colonel Sandurz: One, two, three, four, five.
Skroob: One, two, three, four, five? That’s amazing! I’ve got the same combination on my luggage!
[Colonel Sandurz and Dark Helmet give each other a look.]
Skroob: Prepare Spaceball 1 for immediate departure!
Colonel Sandurz: Yes sir.
Skroob: And change the combination on my luggage!
This is the second in a series of blog posts, the first is on email security.
Overview
Studies have shown that we can remember 2-5 unique passwords, and if it includes special characters or combinations of numbers and letters, we can remember fewer, or none at all. Most people have a single password, or a ‘secure’ password and an un-secure password. As we add more and more site that have personal information which need to be kept ‘secure’ and hackers have access to password information this leads to a problem of easy compromise.
How passwords are stored
Companies store login information in databases, which are stored either at the company itself or on the cloud. Early password techniques (like 1990’s) included storing the password in clear text. So my yahoo account in 2008 had my login ‘bill@kellys.org’ and a password like ‘beagle’. This was stored in something like an excel spreadsheet at yahoo:![]()
3 Million yahoo accounts were hacked in 2008 and these passwords were sold to spammers and hackers. If the website your using can ‘recover’ your password it means they are storing it in the ‘clear’ and it’s completely insecure if they get hacked.
Because this caused a problem, companies moved to encrypt the password with one-way encryption, so now companies might store passwords as:![]()
Today when a company gets hacked this is usually what the hacker ends up with, an encrypted password. This is also why companies can’t recover your password when you lose it because they actually don’t know it.
This isn’t as secure as you think since the hacker can compare this password with 1) dictionary lookups, if you look up the entire websters dictionary is the password found? Can we look up the 1000 most used passwords and is it found? Can we replace a’s with @’s or s’s with $’s etc. and repeat the dictionary search, did we find a match? How about looking up the first 10 million numbers, did we find a match? How about adding a number to the beginning or end of a dictionary word? Computing is cheap and fast and easily accessible to hackers.
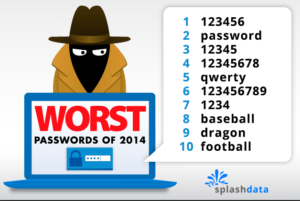
Most common passwords
Yup, lots of people use the word ‘password’ as their password; here are the top 25:
- 56
- 123456789
- qwerty
- 12345678
- 111111
- 1234567890
- 1234567
- password
- 123123
- 987654321
- qwertyuiop
- mynoob
- 123321
- 666666
- 18atcskd2w
- 7777777
- 1q2w3e4r
- 654321
- 555555
- 3rjs1la7qe
- 1q2w3e4r5t
- 123qwe
- zxcvbnm
- 1q2w3e
Please don’t use any of these!
Strong Passwords
Creating strong passwords will help keep your account safe. What’s a strong password?
A password that is difficult to detect by both humans and computer programs, effectively protecting data from unauthorized access. A strong password consists of at least six characters (and the more characters, the stronger the password) that are a combination of letters, numbers and symbols (@, #, $, %, etc.) if allowed. Passwords are typically case-sensitive, so a strong password contains letters in both uppercase and lowercase. Strong passwords also do not contain words that can be found in a dictionary or parts of the user��s own name.
Current common guidelines are 12 to 14 characters long for strong passwords if permitted.
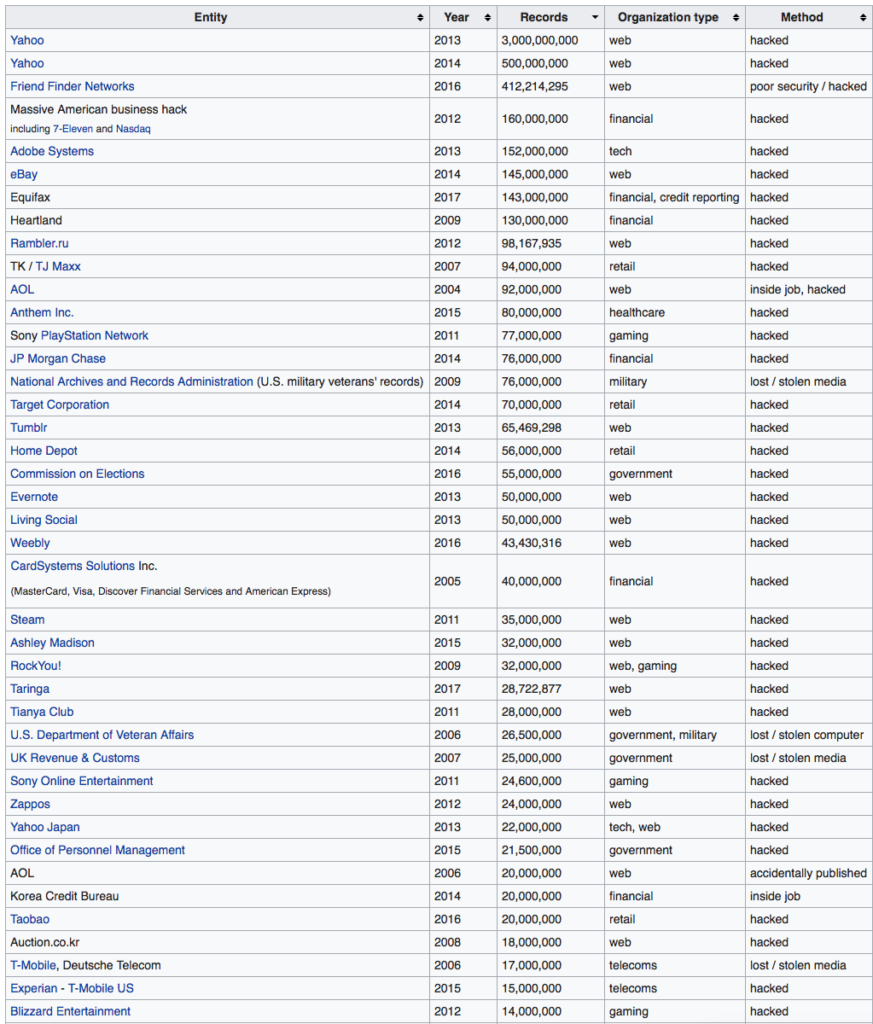
Companies that have been compromised
This list is only the top account hacks of over 13 million users:
from wikipedia:
“This is a list of data breaches, using data compiled from various sources, including press reports, government news releases and mainstream news articles. The list includes those involving the theft or compromise of 30,000 or more records, although many more smaller breaches occur continually. Breaches of large organizations where the number of records is still unknown are also listed. The various methods used in the breaches are also listed, with hacking being the most common.
Most breaches occur in North America. It is estimated that the average cost of a data breach will be over $150 million by 2020, with the global annual cost forecast to be $2.1 trillion.[1][2] It is estimated that in 2015 alone, 707 million records were exposed as a result of data breaches.[3]Vigilante.pw lists over 2,100 websites which have had their databases breached, containing over 2 billion user entries in total.”
Many of the companies you deal with have been hacked and they don’t really have to tell us when that’s taken place. This means if you didn’t lose your favorite password to the 2008 Yahoo hack, someone else has given it to the hackers.
Other ways your password can be hacked
Small devices that record each keystroke on your keyboard could be installed by hackers with physical access. Also virsues from say phishing emails, or zip file attachments could install a keyboard logger and record every keystroke. You MUST use anti-virus software for bothe PC’s and Macs to avoid this unpleasant situation.
Your Password has already been hacked
Yahoo lost millions of clear text password for yahoo accounts in 2008. These password were sold on the dark web for pennies a password. Reliable websites like facebook and wordpress.com, crossed indexed these passwords with their user accounts and warned users who were reusing the same password. So that secure password you’ve been using is probably already compromised.
Unique passwords
In today’s world you need unique passwords for every account that you think would be painful if compromised. So accounts like google, apple, your bank(s), your credit card(s), your financial institution(s), amazon, each of your frequent flyer airline accounts, paypal, nest or other home interconnected devices, ticketmaster, intuit, mint, adobe, hotel reward accounts, you cell phone provider, any charity with your credit card, etc, etc. Basically any organization with your credit card. For me this is over 500 accounts. I can’t remember that many passwords.
Options for multiple secure passwords
You have two bad choices: put your passwords in the cloud with a password manager or come up with a valid secure scheme that can work. My friend who operates in the security universe said “password managers are your least bad bet”. Other schemes, one friend wrote a program that stores passwords, my nephew came up with a program that you type in a secret code, and the name of the website and his code creates a long password based on the name of the website and adds an encrypted ending, for example google.com would be goo12s3Fgh71sd. If you use the same secret code, you get the same password. Most of us won’t be programming a solution. Other solutions involve writing down your password in a password diary, which of course you could misplace. This is not just for your home computer, as we add tablets and smartphones we need password access to each device all the time.
Using a password manager
Laspass.com, dashlane.com, 1password.com are all password managers. I use lastpass.com. Using a password manager requires 1 strong password that should be used ONLY for the password manager, don’t reuse an old password. It’s best if the password is a passphrase like “MyThirdGradeTeacherWasMissBoggianin1969” . As long as you don’t use your mother’s maiden name (probably lost in equifax hack), or any of the common security questions which were also hacked, your good! Many of the password managers have web browser plugins that will fill in passwords for you. So Chrome or Safari or firefox will sense your tying to login to your bank and fill in your username and password. These managers also support IOS and Android devices so you can access passwords on your mobile devices.
Implications of using a password manager
The first implication is a lost master password. Lastpass, and I assume the other password managers, does NOT store your master password. This has profound implications if you can’t remember it. Here is what they say:
- Try logging into the website at https://lastpass.com – if you can sign in here, please uninstall the extension and re-install and test your login again.
- If you can intermittently login: type your Master Password in a text document and copy/paste to ensure there are no typos. In addition, verify whether Caps Lock is enabled or disabled.
- If you still receive an “invalid password” error, try your Password Hint that you set up when you created your account. This is a reminder hint NOT your Master Password.
- If the hint doesn’t help, go to the Account Recovery page to activate your local One Time Password. This allows you to change your Master Password if you’ve logged into LastPass previously on that computer, and is the only way to ‘reset your password’. You should try this on all browsers and on all computers where you’ve used the LastPass plugin to access your account. This method does not work on mobile devices. Account recovery is not supported on mobile devices or apps. Changing the master password, reverting the account, or clearing the browser cache for LastPass can destroy these files.
- If you have updated your Master Password within the last 30 days, you can go through these steps to Revert to change to your previous Master Password. Please note, we do NOT recommend selecting the “restore” option unless you have confirmed with LastPass Support that this is the best course of action.
- If you are only seeing this for your mobile device:
- Verify with the same copy/paste from a plain text document that the password is being entered correctly.
- Please uninstall and re-install the appllication.
- If you have any special characters in your master password, this may be causing the issue as well.
- If you still can’t recover your password, your only recourse is to Reset Your Account and start over. Resetting/deleting permanently removes your data, but your Premium status will be transferred if you use the same email address to set up your new account.
- To recreate your account, go to https://lastpass.com/create_account.php.
yes, that’s pretty serious.
The second implication is to set a recovery family member if you become incapacitated. Since all of your data is now on lastpass, if you become incapacitated it might be critical that someone else could access your account. Lastpass has an emergency access ability. You can list people that you trust and if your account isn’t accessed in a time you set (like a week or a month) the trusted person can gain access.
The third implication is if it’s convenient then it’s unsecure. If your using browser plugins then you need to secure the equipment that it’s running on. Because you can log into your password manager on a browser, you can expose your passwords to people using your computer. So you need to NOT let others use your computer. So your PC or Mac need a password to access it, AND you need to use a password when your computer goes to sleep. Also, your phones and tablets should also have a passcode to unlock them.
Summary of password managers:
- Use a password manager
- Select a long memorizable passphrase as a master password
- set trusted people for emergency access
- set a password or passcode on all of your computers, phones and tablets
- Only allow people you trust to use your devices
- change all your critical passwords to computer generated passwords
- search for any duplicate passwords in your password manager and change them to unique passwords
Fear of cloud based password managers
Many people fear putting all their password eggs in one basket with a password manager. This comes back to my friend who said “password managers are your least bad bet”. They do a very good job at securing your data which is why you can’t easily recover it if you forget your master password. Here is how lastpass (and by extension other password managers work:
LastPass is a browser extension that generates, stores, and fills in passwords. It makes practicing good security a little easier, by letting you generate unique, random, very long passwords for each website you go to. If one website is compromised, attackers only have access to your account on that one website, and only until you change the password.
On the backend, the security of your LastPass vault hinges on the “master password”. When you create your LastPass account, the vault is encrypted with the master password. The master password, thus, is the key to the vault, which is protected by mathematics. For a decent password, it would take longer than the age of the universe to crack your password and enter your vault. On top of this, LastPass artificially makes logging in take *much* more time (on the order of a few seconds, but this adds up to billions of years for a brute force attack) and thus more difficult to attack.
LastPass never sees the “raw” contents of your vault. When you log in, your master password is scrambled through a one-way hash function, and sent to LastPass. LastPass compares this with the hash they have on file, and if everything checks out, they send your encrypted vault to your computer. Your computer then decrypts your vault using the master password, and stores it for the duration of your session.
In the unlikely event that LastPass is compromised, or LastPass receives a government request for your information, all LastPass has is your hashed master password, and an encrypted vault. These are both absolutely worthless without the master password itself. The only way around this is to try every possible password to see if it matches the hashed version. This is why resetting your LastPass master password also empties your vault.
Answering Security Questions
Unfortunately with the hacks to all these corporate websites, your ‘security questions’ have almost certainly been hacked. This means that people can probably guess who your best friend is, what your mother’s maiden name is, etc. A password manager has a solution for you: LIE. Password managers have a ‘notes’ field that you can enter notes, so list the security questions of each website and list your answers. Don’t answer truthfully, and they don’t check so you can come up with the same answer for each question. Then put all the questions and answers into the secure note.
Securing the secure account
After you’ve secured your accounts with secure passwords, you SHOULD enable a relatively new security feature. When you log into a site from a new computer or device, some sites will ask for a second comfirmation usually by sending a text message to your smartphone or asking you to confirm with a smartphone application. This is called two factor authentication (2FA), or multi-factor authentication (MFA). Google, Apple, facebook, twitter, yahoo, and many others allow for 2 factor authentication you should use it when ever possible.
A few implications of using 2 factor authentication you should think about, first, you might want to turn lock screen notification of text messages OFF so that people with access to your locked phone can’t see the authentication code. Second, if you travel internationally, and use a new phone SIM card while in country, like for extended trips to Israel or other overseas locations, your text messages will not be delivered.
Checklist:
- Use unique passwords on every site
- Use strong passwords on every site
- stop using your old passwords
- Therefore, use a password manager
- Use a long passphrase that has never been used before for the password manager
- Set emergency access for the password manager
- Set passwords and passcodes on every computer, smartphone, and tablet you own
- Never answer security questions truthfully and keep track of each question and answer in a password manager
- Enable 2 factor authentication wherever possible
The last blog post in this series is how to deal with the Equifax hack specifically.



One thought on “Passwords as primary computer security”